LDAP#
The LDAP feature allows you to configure a connection to a directory service. Through this connection, you can import either roles and associated users or users for existing roles in nJAMS Server or both. Authentication of an imported user will be done by the directory service. Authorization will be done via the access rights associated with the roles of the user.
The import of users and roles can be made ad hoc or scheduled via a configurable job. In both cases, all configured roles and users will be read from the directory service and created or updated in nJAMS Server. Roles or users which were formerly imported but do not longer match the configuration will be removed from nJAMS Server. See chapter ‘System Control > Jobs > LDAPSynchronization’ for learning how to configure a scheduled job for periodic import.
Roles imported from a directory service cannot be changed in nJAMS Server except for the granting and revoking of access right. Users must be linked to these roles in the directory service. They cannot be assigned to an imported role in nJAMS Server. Users imported from a directory service cannot be changed in nJAMS except for the roles to which the users is associated. An imported user can be added to or removed from a role created in nJAMS Server but not to a role imported from the directory service. This has to be done inside of the directory service. As the login will be done against the directory service via LDAP, the password cannot be changed in nJAMS Server.
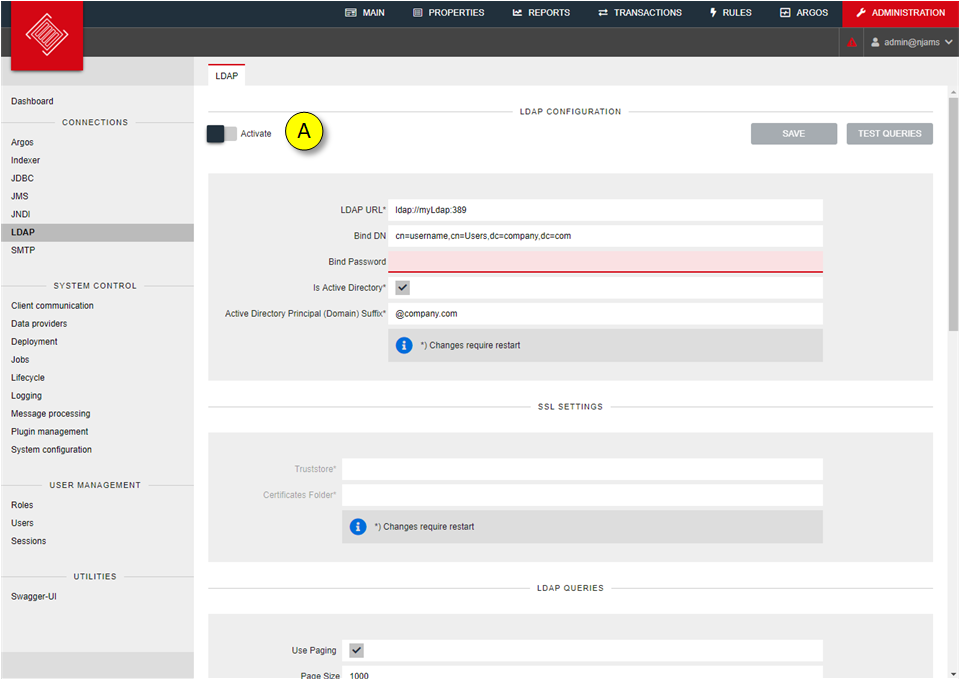
To access a directory service you have to configure a LDAP connection by providing a host URL and optional a user name respectively a bind DN and a password. This depends on the setting of your directory service. After the connection has been configured you may test if the connection can be established.
If you want to import roles from LDAP, you need to create a LDAP query and attribute mappings for both the roles and their associated users. If you want to import users to already existing roles you need to create a LDAP query and a user attribute mapping on the LDAP tab of the role (see Receiving Users from a directory service).
For a LDAP query you need both a query string and a search base.
For importing roles, at least a mapping for the role name is required. A role comment may optionally be mapped.
You shall also give a user query string and at least a mapping for the user names to import users associated with the imported roles. The mapping of the first name, last name, email and a comment are not mandatory. Because these fields cannot be changed in nJAMS Server you will have to map these fields too, if needed.
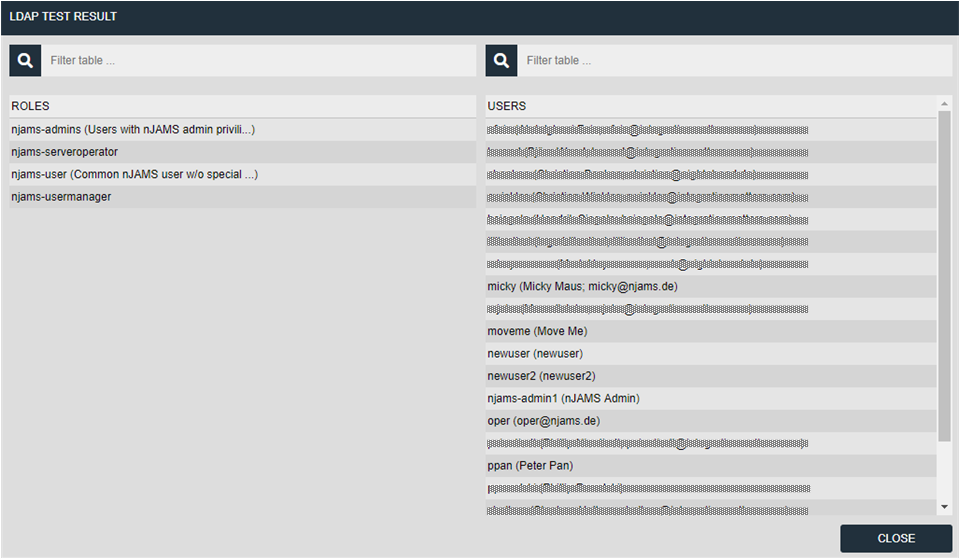
You can test your query and mapping with the test button. You will see the roles from your directory service that matches your role query. Click on role name to see the users associated to that role for your user query and mapping:
When the test is successful, save the settings.
Due to the name of roles and users in nJAMS Server must be unique, the identification of a user or role always takes place by the mapped name and not by the distinguished name (DN). The DN of an imported user or role will be shown on the role or user page.
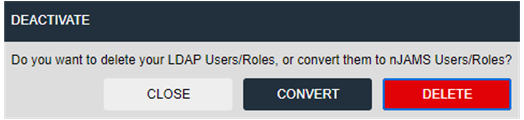
Activate starts synchronization of LDAP. Deactivate removes LDAP sychronization and asks to convert or remove synchronized users/roles.
- alt:
Deactivate synchronization
- LDAP over SSL:
You can use LDAP over SSL to secure your LDAP connection. Please prepare the following:
Make sure your LDAP Server is prepared to allow LDAP over SSL (LDAPS).
Export the Root CA Certificate as base64 encoded X.509 file, which signed the LDAP Server certificate
In the LDAP dialog enter a LDAPS connection and either the path to the Truststore or the folder that contains the certificate:
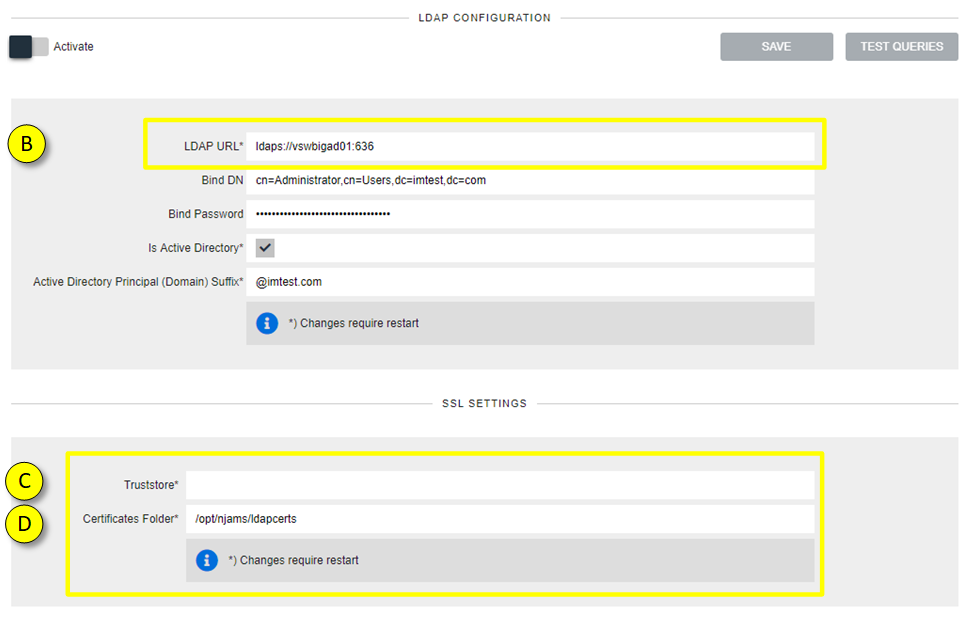
LDAP URL: Enter the LDAPS connection to your LDAP Server. As soon as you enter “ldaps”, the SSL Settings below are available for input.
Truststore: enter full path to your trustrore file that contains the certificate.
Certificates Folder: Alternatively enter the path to the folder that contains the certificate, e.g. /opt/njams/ldapcerts/.
Please restart nJAMS Server for the changes to take effect.